The Cyber-Secure Supply Chain

The need to ensure supply chains are cyber-secure is primary – and immediate. read on to know more:
That cybersecurity is central to the smooth functioning of supply chains is a fact well known. Recent global events, such as the pandemic, geopolitical shifts, and extreme weather incidents, have underscored the necessity of supply chain resilience. In parallel, cyberattacks on corporate supply chains are on the rise in terms of both frequency and sophistication. Notably, the Ponemon Institute reports that 98% of companies have experienced negative consequences due to breaches originating within their network.
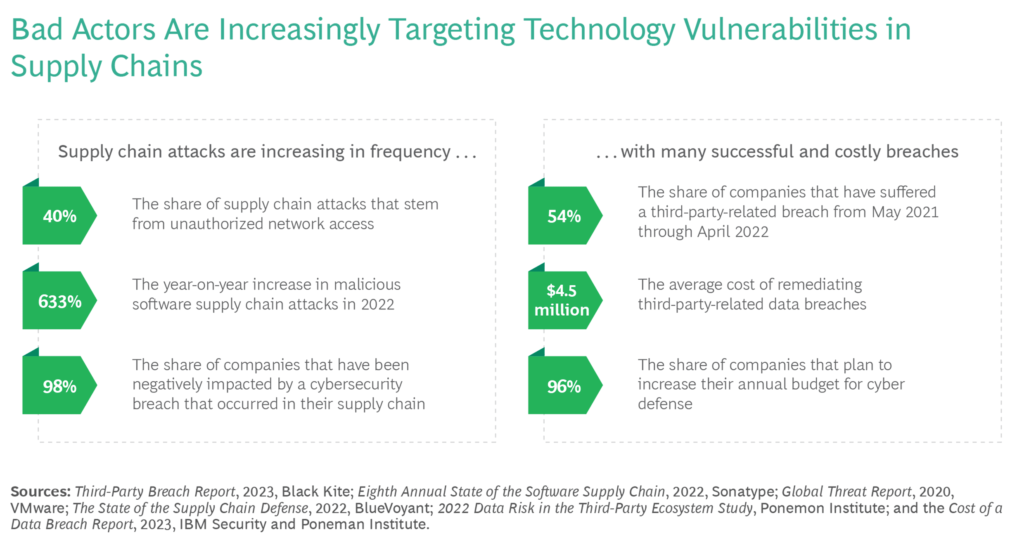
Image: Cyber-vulnerabilities in Supply Chains; Source: BCG
Understanding Complexity
The complexity of modern supply chains and digital networks lies at the heart of the escalating cyber threats. These networks often involve multiple tiers, where companies depend on a multitude of vendors, service providers, and customers, who, in turn, rely on their suppliers. Consequently, a company’s supply chain is intrinsically linked to its digital ecosystem, creating a ripple effect of cybersecurity risks.
Cloud networks play a significant role in this complexity as companies increasingly shift their workloads to public or private clouds, relying on cloud providers’ security controls. This transition can reduce visibility into potential risks. Furthermore, the proliferation of internet-of-things (IoT) devices connected to these networks adds additional vulnerabilities. As companies embrace electronic tools and devices, the threat landscape expands.
The modern threat landscape also sees malicious actors employing more advanced tools and techniques to exploit digital network vulnerabilities. Even organizations with robust cybersecurity capabilities can fall victim to less sophisticated third parties connected to their networks. A prominent example of a sophisticated supply chain breach was the SolarWinds attack in 2020, which affected numerous private companies and government agencies in the US and Europe. This breach exploited a routine software update, exposing the vulnerabilities inherent in interconnected supply chains.
Another example is the Meltdown and Spectre vulnerabilities, which plagued companies worldwide. These attacks had persisted within central processing units’ design for years before discovery in 2018.
A Proactive Strategy
Despite the growing threat and sophistication of cyberattacks, companies can mitigate their risks and associated costs through proactive cybersecurity management. Given the urgency and scale of the task at hand, adopting such an approach entails the following steps, according to the Boston Consulting Group:
- Initiating a Risk Management Program: The first and often most challenging step is getting a risk management program up and running. Despite the initial difficulties, taking this crucial step sets your company far ahead of organizations with no such program in place. Begin by assessing your supply chain and identifying quick-win opportunities – vulnerabilities that can be swiftly addressed to enhance network security. It’s important to note that the solution may not be flawless, but initial imperfections are to be anticipated, not feared.
Companies equipped with a cybersecurity program have a significant advantage over those without one.
- Integrating the Program into a Comprehensive Risk Management Strategy: To gauge the extent of your exposure, it’s beneficial to develop scenarios for different types of cyberattacks on various supplier types. Determine the minimum information required to understand your suppliers’ risk exposure, assess the potential impact on the supply chain, and assign vendors to different risk tiers. Suppliers in higher-risk tiers may warrant a more in-depth risk assessment or stronger security controls.
For instance, a major consumer products company executed an extensive plan to implement cybersecurity risk management practices within its supply chain. These practices included a technology-backed tiering approach that automatically prioritized high-risk vendors based on cybersecurity-related criteria. This approach not only improved sourcing processes and tools but also facilitated the enhancement of customer and vendor systems with minimal disruption.
- Leveraging Existing Tools: Explore your organization’s existing enterprise resource planning software and other systems for untapped capabilities that can support the development of your risk management program. Consider integrating a cybersecurity risk-tiering process or controls directly into your software.
- Adopting Phased Implementation: In larger organizations, the sheer number of third-party entities can pose a significant challenge to implementing a risk management program all at once. Instead, consider a phased approach by prioritizing regions, business units, or product lines that involve third parties with higher risk levels. You can also pilot segments of the program with new customers or vendors, or a select group of existing ones. For example, you might test a new screening process with new vendors before expanding it to other third parties. Insights gained during the onboarding of new parties, particularly regarding common risks or vulnerabilities, can be invaluable in assigning risk tiers to the remaining entities.
- Collaboration Across Functions: Enhancing supply chain security requires a collaborative effort across various functions within the organization. It’s essential to involve not only the technology and risk functions but also business units directly engaging with third-party vendors and customers, as well as those responsible for product, procurement, merchandising, and privacy.
- Data-Driven Decision-Making: The program’s evaluation and adjustment should be driven by data. An effective approach involves identifying vendors willing to provide feedback before program implementation. Regular evaluations should be conducted to gauge its effectiveness. This assessment process may include analysing sample data to ensure the appropriate assignment of third parties to the right risk tiers and the accurate assessment of threat details, avoiding both over-analysis and under-analysis.
- Securing Visible Support from Senior Leadership: The success of a cybersecurity risk management program for the supply chain hinges on the prioritization and backing of senior leadership, including sufficient funding. Encourage involvement from leaders in tabletop cybersecurity risk exercises, potentially involving interactions with third parties. This not only underscores the program’s importance but also fosters cooperation.
Cybersecurity risk is a paramount challenge facing organizations today, with thousands of companies annually suffering costly breaches originating from third-party vulnerabilities. Supply chains and digital networks with multiple tiers present a complex risk landscape. To enhance supply chain resilience, companies should adopt a proactive cybersecurity risk-management program, reinforcing the practices and policies of third parties in their supply chain. While this endeavour may seem daunting, it represents a highly effective strategy for improving supply chain resilience and proactively preventing organization-wide breaches.


