Fighting Malware with Deep Learning

A recent study on deep learning and API-based malware detection marks the newest notable breakthrough in cybersecurity, offering unmatched accuracy and efficiency. As cyberthreats evolve, integrating AI-driven solutions into everyday security measures is essential. With rapid advancements in AI and machine learning, the future of malware detection promises a proactive defence against ever-adapting cyberthreats
Android, the world’s most widely used mobile operating system, is also one of the most vulnerable. Its open architecture and expansive app ecosystem make it highly susceptible to sophisticated malware attacks designed to bypass traditional detection methods. With millions of new Android malware samples emerging annually, security professionals face an ongoing battle to stay ahead of these ever-evolving threats with conventional detection techniques increasingly falling short in identifying and mitigating these advanced attacks.
A recent study by Wei Sun, a researcher at the School of Information Engineering, Heilongjiang Polytechnic, presents a new paradigm for malware detection using deep learning and API call analysis. Published in the EURASIP Journal on Information Security (2025), the study explores how heterogeneous graph modelling and relational graph convolutional networks (R-GCNs) can significantly improve malware detection accuracy and efficiency.
The Problem with Traditional Malware Detection
Traditional malware detection techniques are broadly classified into two types:
- Signature-Based Detection: This method relies on predefined malware signatures stored in databases. While effective against known threats, it struggles with new and evolving malware variants.
- Behavioural Analysis: This approach monitors an application’s behaviour in real-time, identifying suspicious activities. However, it is resource-intensive and slow, making it unsuitable for large-scale deployment.
Despite these approaches, malware developers have found ways to bypass detection using code obfuscation, polymorphism and adversarial attacks. To address these limitations, Sun’s research introduces a deep learning-based solution that enhances detection accuracy while maintaining efficiency.
Key Innovations in the Research
One of the most significant advancements in this study is the use of heterogeneous graph modelling for malware detection. Traditional methods often treat API calls as isolated events, limiting their ability to capture the full behavioural context of an application. This study overcomes that limitation by constructing structured graphs that encode relationships between API functions, entry points, and overall application behaviours. By doing so, the model can better distinguish between benign and malicious software, making detection more precise and reliable.
Another crucial innovation is the application of Relational Graph Convolutional Networks (R-GCNs) to analyse API call dependencies. Unlike conventional approaches that simply extract API usage frequencies, this model leverages positional encoding to detect subtle behavioural anomalies. By understanding the sequence and relationships of API calls within an application, the system can flag suspicious activity with much higher accuracy.
To further enhance detection capabilities, the study introduces efficient feature extraction techniques. Instead of using frequency-based analysis, the model embeds API call sequences into a high-dimensional space. This ensures that important contextual and sequential information is preserved. The inclusion of positional encoding helps the model recognise not just which API calls are made but also in what order–an essential factor in identifying malicious intent.
Validating the Model: Superior Accuracy and Performance
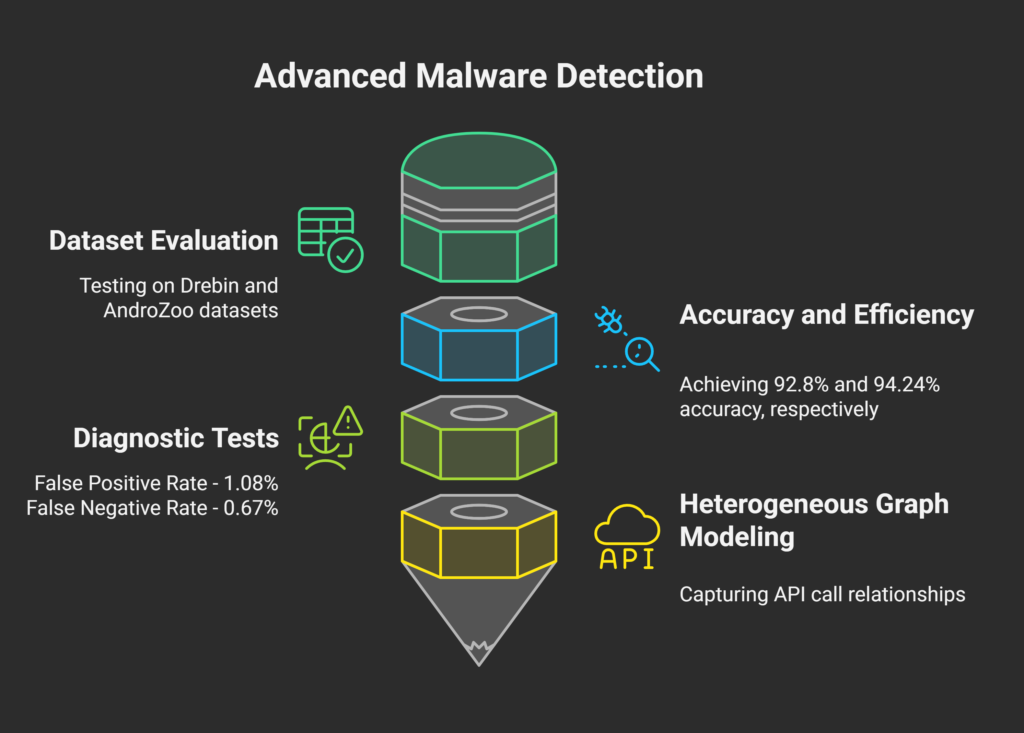
To evaluate the effectiveness of the proposed method, the study was tested on two well-established malware datasets: Drebin and AndroZoo. Drebin includes 5,560 malicious samples and 9,476 benign applications, while AndroZoo is a vast repository containing millions of APK files collected from various Android marketplaces. These datasets provide a comprehensive testbed to assess the robustness and efficiency of the model.
The results indicate that the deep learning-based approach significantly outperforms traditional methods. The model achieved an accuracy of 92.80% on the Drebin dataset and 94.24% on AndroZoo, demonstrating strong generalisation capabilities across different malware environments. Beyond accuracy, the model was also highly efficient, taking only 5–10 seconds to classify an application. Additionally, it exhibited a False Positive Rate (FPR) of 1.08% and a False Negative Rate (FNR) of 0.67%, significantly reducing false alarms and enhancing reliability compared to conventional detection strategies.
What sets this approach apart from previous research is its ability to capture the contextual relationships between API calls through heterogeneous graph modelling. Traditional signature-based methods rely on predefined malware patterns, making them ineffective against new, evolving threats. Machine learning-based approaches improve upon this by analysing extracted features, but they often struggle with understanding API call dependencies and behavioural sequences. In contrast, Sun’s deep learning approach – particularly the use of R-GCNs – effectively models these relationships, allowing for more accurate and dynamic malware detection. With a 94.24% accuracy rate, this method establishes itself as a superior alternative to existing techniques, combining high precision with computational efficiency.
Real-World Applications and Future Prospects
The adoption of this advanced malware detection approach has the potential to revolutionise cybersecurity in several ways:
- Real-Time Mobile Security: Android security apps could integrate this method to scan new applications before installation, preventing infections in real-time.
- Enterprise Cybersecurity Solutions: Organisations could use this model to monitor applications running within corporate environments, identifying suspicious activities before they cause harm.
- Zero-Day Threat Detection: Unlike signature-based methods, this approach can detect never-before-seen malware variants, improving overall security posture.
- IoT Security Enhancement: Internet of Things (IoT) devices running Android-based systems could benefit from this approach, ensuring that connected devices remain secure.
While the study presents a highly promising method, there are still areas that require further research:
- Scalability Issues: Deep learning models are computationally intensive, requiring powerful hardware for large-scale analysis.
- Adversarial Attacks: Hackers could develop countermeasures to trick AI-based malware detectors, necessitating continuous model updates.
- Explainability: AI-driven security tools often function as black boxes, making it difficult for cybersecurity professionals to interpret decisions.
Future research should focus on optimising model efficiency, developing adversarial-resistant techniques, and improving the interpretability of AI-based malware detection systems.
Source: Sun, W. (2025). Malicious Software Identification Based on Deep Learning Algorithms and API Feature Extraction. EURASIP Journal on Information Security.


